TLS 1.2 Security Protocol
Updating configuration for PMG Connectors

The world of technology is fast-moving and ever-changing. While it may not always seem worthwhile to keep up with the Joneses, when it comes to security, it’s necessary to stay on the forefront.
More and more external systems are enforcing TLS 1.2 security protocol and no longer supporting previous TLS versions. If this is happening in your organization, don’t fret. PMG connectors can be configured to support TLS 1.2 in most cases.
How do you know if you need to update your connector configuration to support TLS 1.2?
Well, hopefully the owner of the other system would notify your internal PMG team of a pending update to TLS 1.2 protocols, giving you advance warning and plenty of time to address. But in the real world, that doesn’t always happen, and you may see errors in your connector actions as a result.
Here’s a sampling:
• The underlying connection was closed: An unexpected error occurred on a send.
• Inner Exception: Unable to read data from the transport connection. The connection was closed.
• An existing connection was forcibly closed by the remote host.
There are two methods you can use to update your connector configuration for TLS 1.2.
1) If your organization maintains your connector config file on your app server in the path \Program Files\PMG Service Catalog\SPE\, then you will want to open and update the connector config file in that location. Below is a sample scenario in which the bold portion sets which protocol should be enabled or disabled for the scenario.
< scenario name=”PMG_Test” adminport=”48989″ domain=”TESTDOMAIN” password=”abcxyz123″ username=”testuser@pmgnet.dev” baseurl=”https://pmgtest.sharepoint.com/sites/” locale=”online” tls=”false” tls11=”false” tls12=”true” ssl3=”false”/>
2) If your organization maintains connector scenarios through the Connector Config Management UI, you would make the update through the UI. Below is a sample scenario. Note that tls12 is set to true, while the other tls settings are set to false.
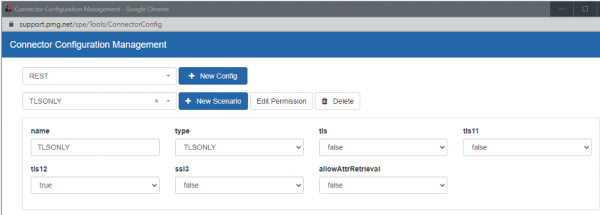
These simple updates will ensure that you’re keeping up with the latest security protocols for your connectors. Be safe out there!
